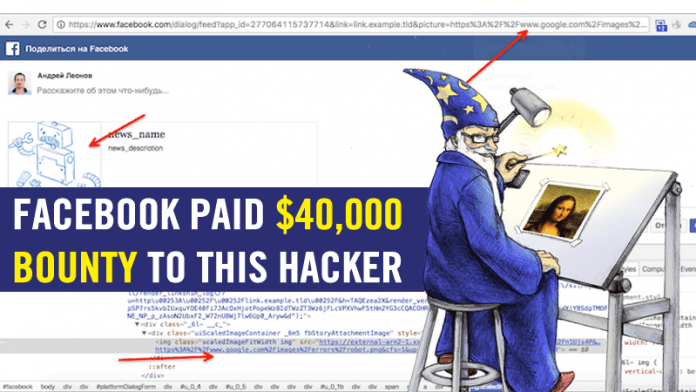
Bug hunter Andrey Leonov claims that Facebook issued him $40,000 bug bounty for gaining remote code execution on its servers using ImageMagick flaw.
Facebook Paid $40,000 Bounty To This Hacker!
First of all, let me tell you about ImageMagick it is a free and open-source software suite for displaying, converting, and editing raster image and vector image files. It can read and write over 200 image file formats.
As reported by The Register, a Flaw in ImageMagick was found at the end of April 1, 2016, in which the tools could be abused to allow attackers to upload malicious images that grant remote code execution from where many further compromise, data exfiltration, and lateral movement may be possible.
Now it looks like a hacker has gained remote code execution on its servers using that ImageMagick flaw. Andrey Leonov has shared a blog post in which he had disclosed how he learned remote code execution on Facebook’s server using the flaw.
The hacker has given all the details, except the sensitive proof-of-concept exploit. Hackers claim that he discovered the flaw accidentally when another service to Facebook redirected him, then he decided to look whether the ImageMagick flaw was left unpatched.
@Facebook #ImageTragick remote code execution https://t.co/Rk3Qtax3ZD #RCE #BugBounty
— Andrew Leonov (@4lemon) January 17, 2017
“For full proof that exploit works, I provided Facebook security team with result of cat /proc/version output which is not going to publish here”
Andrey Leonov said “Once upon a time on Saturday in October i was testing some big service (not Facebook) when some redirect followed me on Facebook. It was a «Share on Facebook» dialog,”
“I am glad to be the one of those who broke the Facebook”. Andrey Leonov claims that he received a $40,000 bounty from Facebook, which looks like the highest bounty figure paid by Facebook. Andrey Leonov reported the vulnerability on 16 October 1, 2016, and he got the reward on 28 October 2016.
So, what do you think about this? Share your views in the comment box below.